| [ Team LiB ] |
|
9.3 Using the .NET Framework Configuration ToolThe .NET Framework Configuration tool (Mscorcfg.msc) is a Microsoft Management Console (MMC) snap-in supplied with the .NET Framework that provides a graphical interface to manage various aspects of .NET configuration. We are concerned with the administration of security policy only and will not discuss the other features (refer to the .NET Framework documentation).
The steps to execute Mscorcfg.msc from the Windows user interface depend on the operating system you are using:
Regardless of the operating system you choose, you can start Mscorcfg.msc from the command line using the following command, where version is the version of the .NET framework, such as "v1.0.3705" for Version 1.0: %Systemroot%\Microsoft.NET\Framework\version\Mscorcfg.msc Figure 9-2 shows the main window of Mscorcfg.msc. Expanding the Runtime Security Policy node of the console tree, you will see child nodes for each of the enterprise, machine, and user policy levels. Figure 9-2. The Mscorcfg.msc main window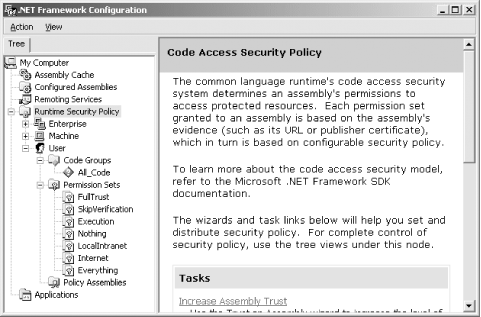 By expanding the node representing the policy level you want to administer, you can see three subtrees, one for each of the following policy-level elements we discussed in Chapter 8:
The following sections focus on the management of these three elements. 9.3.1 Managing Fully Trusted AssembliesIn Chapter 8, we explained the requirement for policy levels to define a list of fully trusted assemblies. By right-clicking the Policy Assemblies node, as shown in Figure 9-3, a shortcut menu provides you with the following options:
Figure 9-3. Managing fully trusted assemblies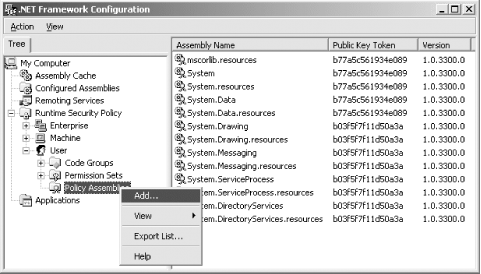 9.3.1.1 Adding a fully trusted assemblyBefore you can add a new assembly to the fully trusted assemblies list, you must install the assembly into the global assembly cache. In Chapter 2, we discussed the global assembly cache and how to add assemblies to it. After you have installed the assembly in the global assembly cache, right-click the Policy Assemblies node of the console tree, as shown in Figure 9-3 and select Add... from the shortcut menu. The Choose Assembly From Assembly Cache dialog box (shown in Figure 9-4) is displayed, listing all of the assemblies installed in the global assembly cache. Select the assembly you want to make fully trusted and click the Select button. Figure 9-4. List of assemblies in the global assembly cache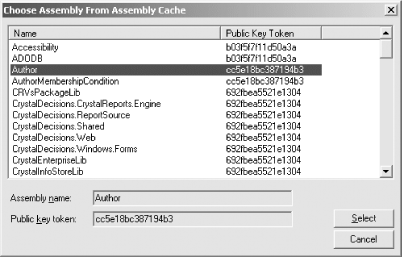
9.3.1.2 Deleting a fully trusted assemblyTo remove an assembly from the fully trusted assemblies list, make sure the righthand pane of the console displays the current list of fully trusted assemblies, as previously shown in Figure 9-3. To configure this, right-click the Policy Assemblies node in the console tree and click View followed by Assemblies from the shortcut menus. With the list displayed, right-click the assembly that you want to remove and select Delete from the shortcut menu that appears. You will be prompted to confirm the delete action; click the Yes button and the assembly is removed.
9.3.2 Managing Named Permission SetsBy expanding a policy level's Permission Sets node in the console tree, you will see the list of named permission sets defined in that policy level. Figure 9-5 shows the list of named permission sets defined in the default user policy. Figure 9-5. Managing named permission sets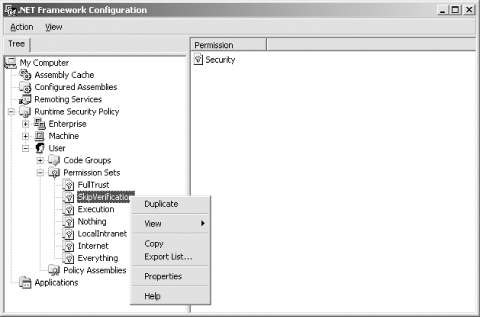 As shown in Figure 9-5, right-clicking any of the default permission set nodes displays a shortcut menu containing the following options:
The shortcut menu for the default Everything permission set or any other non-default permission set includes these additional options:
9.3.2.1 Creating named permission setsTo create a new named permission set, right-click Permission Sets node in the console tree and select New... from the shortcut menu. The Create Permission Set dialog box, shown in Figure 9-6, appears. You have two options for creating the new permission set: manual creation using the graphical interface or importing the definition of the permission set from an XML file. Figure 9-6. Creating a new permission set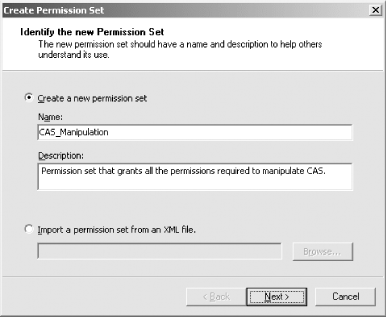 To import the named permission set from a file, select the Import a permission set from an XML file radio button, enter the name of the file containing the definition, and press the Next button. The XML description of the permission set must have the structure shown in the following example, which describes a permission set named TestSet containing the unrestricted FileIOPermission, as well as the Assertion and Execution permissions from SecurityPermission: <PermissionSet class="System.Security.NamedPermissionSet"
version="1"
Name="TestSet">
<IPermission class="System.Security.Permissions.FileIOPermission, mscorlib,
Version=1.0.3300.0, Culture=neutral, PublicKeyToken=b77a5c561934e089"
version="1"
Unrestricted="true"/>
<IPermission class="System.Security.Permissions.SecurityPermission, mscorlib,
Version=1.0.3300.0, Culture=neutral, PublicKeyToken=b77a5c561934e089"
version="1"
Flags="Assertion, Execution"/>
</PermissionSet>
The complexity of information in the XML description of a named permission set means that it is easier to create this information programmatically. This is easy to do by creating a System.Security.NamedPermission object, populating it with permission objects, and calling the ToString method on the System.Security.SecurityElement returned by the ToXml method. The following code demonstrates the creation of the TestSet named permission set (whose XML description we just listed) and displays it to the console: # C#
// Create an empty NamedPermissionSet
NamedPermissionSet ps = new NamedPermissionSet("TestSet", PermissionState.None);
// Add an unrestricted FileIOPermission
ps.AddPermission(new FileIOPermission(PermissionState.Unrestricted));
// Add a SecurityPermission with Assertion and Execution permissions
ps.AddPermission(new SecurityPermission(SecurityPermissionFlag.Assertion |
SecurityPermissionFlag.Execution));
// Display an XML version of the named permission set to the console.
Console.WriteLine(ps.ToXml( ).ToString( ));
# Visual Basic .NET
' Create an empty NamedPermissionSet
Dim ps As NamedPermissionSet = _
New NamedPermissionSet("TestSet",PermissionState.None)
' Add an unrestricted FileIOPermission
ps.AddPermission(New FileIOPermission(PermissionState.Unrestricted))
' Add a SecurityPermission with Assertion and Execution permissions
ps.AddPermission(New SecurityPermission(SecurityPermissionFlag.Assertion Or
SecurityPermissionFlag.Execution))
' Display an XML version of the named permission set to the console.
Console.WriteLine(ps.ToXml( ).ToString( ))
Instead of importing the named permission set, you can create it manually by selecting the Create a new permission set radio button. Enter a name and a description for the new permission set. In Figure 9-6, we entered the name "CAS_Manipulation" because we are creating a permission set that includes all of the permissions necessary to manipulate CAS programmatically. Press the Next button to display the dialog box shown in Figure 9-7, which allows you to select the set of permissions to include in the permission set. Figure 9-7. Assigning permissions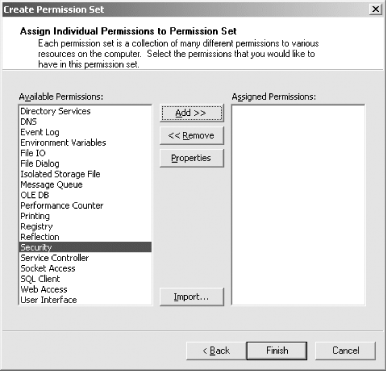 Select the permission you want to include in your permission set from the Available Permissions list and click the Add button. You will see a Permission Settings dialog box. The contents of this dialog box depend on which permission you selected to add. Figure 9-8 shows the Permission Settings dialog box for the Security permission, which represents the System.Security.Permissions.SecurityPermission class we described in Chapter 7. Figure 9-8. Configuring permissions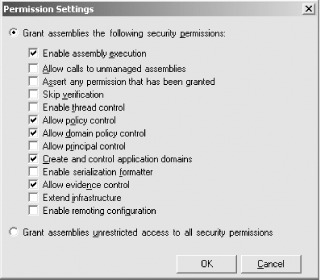 In Figure 9-8, we select the individual elements of the SecurityPermission that we want to include in the new permission set. The permissions we have selected here map to the Execution, ControlPolicy, ControlDomainPolicy, ControlAppDomain, and ControlEvidence members of the System.Security.Permissions.SecurityPermissionFlag enumeration, which is also discussed in Chapter 7. Pressing the OK button takes you back to the list of available permissions shown in Figure 9-7. You can add more permissions or remove any that you have already added. Figure 9-7 also shows a button named Import... (which allows you to import an individual custom permission to your permission set). Pressing the Import... button displays a dialog box that allows you to select the file containing the XML description of the custom permission. The XML description of the permission must be of the appropriate structure to allow the runtime to create an instance of the permission using the permission class's FromXml method. The following example contains the XML description of the custom RadioPermission class that we developed in Chapter 7. This specific example grants access to turn the radio on and off: <IPermission class="OReilly.ProgrammingDotNetSecurity.RadioPermission,
Radio, Version=1.0.0.0, Culture=neutral, PublicKeyToken=cc5e18bc387194b3"
version="1"
StartStop="true"/>
After configuring the contents of the new permission set, clicking Finish returns you to the main Mscorcfg.msc window.
9.3.3 Managing Code GroupsBy expanding a policy level's Code Groups node in the console tree, you will see the root code group for the policy level, as shown in Figure 9-9. Figure 9-9. Managing code groups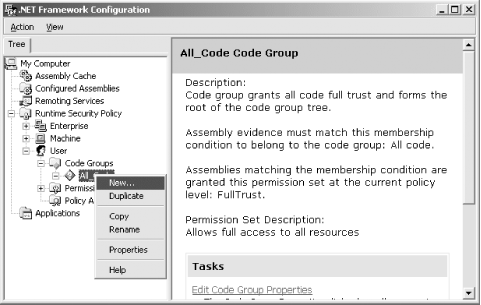
Right-clicking the root code group brings up a shortcut menu with the following options:
By expanding the node representing the root code group, and the subsequently displayed child nodes, you can navigate through the code group hierarchy of the policy level. Right-clicking any code group node (except the root node) displays a shortcut menu the same as that we have already described, but with the following two additional options:
9.3.3.1 Creating code groupsTo create a new code group, right-click the existing code group under which you want to create the new child code group and select New... from the shortcut menu.
In the Create Code Group dialog box shown in Figure 9-10, you have the option to create the new code group manually or to import an XML description of the code group from a file. Figure 9-10. Identifying the new code group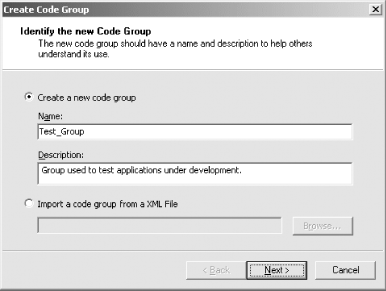 To import a code group from a file select, the Import a code group from a XML file radio button, enter the name of the file containing its XML description, and press the Next button. The XML description of the code group must have the structure shown in the following example, which defines a code group with the configuration listed in Table 9-3: <CodeGroup class="System.Security.Policy.UnionCodeGroup, mscorlib, Version=1.0.3300.
0, Culture=neutral, PublicKeyToken=b77a5c561934e089"
version="1"
Attributes="Exclusive"
Name="TestGroup"
Description="A code group for testing">
<IMembershipCondition class="System.Security.Policy.SiteMembershipCondition,
mscorlib, Version=1.0.3300.0, Culture=neutral, PublicKeyToken=b77a5c561934e089"
version="1"
Site="*.oreilly.com"/>
<PermissionSet class="System.Security.NamedPermissionSet"
version="1"
Name="FileAccess">
<IPermission class="System.Security.Permissions.FileIOPermission, mscorlib,
Version=1.0.3300.0, Culture=neutral, PublicKeyToken=b77a5c561934e089"
version="1"
Unrestricted="true"/>
</PermissionSet>
</CodeGroup>
As with the permission set you imported in Section 9.3.2.1, the complexity of a code group's XML description means it is easier and less error-prone to create. We detail the programmatic creation and configuration of code groups in Chapter 8. As an example, here is the code that will generate the TestGroup code group we just described and print an XML representation of it to the console: # C#
// Create the named permission set and add unrestricted file access.
NamedPermissionSet pset =
new NamedPermissionSet("FileAccess",PermissionState.None);
pset.AddPermission(new FileIOPermission(PermissionState.Unrestricted));
// Create the policy statement and set the Exclusive attribute.
PolicyStatement pstate =
new PolicyStatement(pset, PolicyStatementAttribute.Exclusive);
// Create the membership condition to match all "*.oreilly.com" sites.
IMembershipCondition mcon = new SiteMembershipCondition("*.oreilly.com");
// Create and configure the UnionCodeGroup
UnionCodeGroup cg = new UnionCodeGroup(mcon, pstate);
cg.Name = "TestGroup";
cg.Description = "A code group for testing";
// Display the CodeGroup to the console
Console.WriteLine(cg.ToXml( ).ToString( ));
# Visual Basic .NET
' Create the named permission set and add unrestricted file access.
Dim pset As NamedPermissionSet = _
New NamedPermissionSet("FileAccess",PermissionState.None)
pset.AddPermission(New FileIOPermission(PermissionState.Unrestricted))
' Create the policy statement and set the Exclusive attribute.
Dim pstate As PolicyStatement = _
New PolicyStatement(pset,PolicyStatementAttribute.Exclusive)
' Create the membership condition to match all "*.oreilly.com" sites.
Dim mcon As IMembershipCondition = _
New SiteMembershipCondition("*.oreilly.com")
' Create and configure the UnionCodeGroup
Dim cg As UnionCodeGroup = New UnionCodeGroup(mcon,pstate)
cg.Name = "TestGroup"
cg.Description = "A code group for testing"
' Display the CodeGroup to the console
Console.WriteLine(cg.ToXml( ).ToString( ))
Instead of importing the code group, you can create it manually using a series of dialog boxes by selecting the Create a new code group radio button, and entering a name and a description for the new code group. In Figure 9-10, we entered the name "Test_Group" to create a code group that we will use to grant permission to applications we are in the process of developing. Press the Next button to display the dialog box shown in Figure 9-11, which allows you to configure the membership condition for the new code group. The graphical interfaces allow you to base membership on any of the standard evidence types we discussed in Chapter 6. Figure 9-11 shows the use of Url evidence to match any code loaded from the c:\development\cas_project directory. Figure 9-11. Specifying a membership condition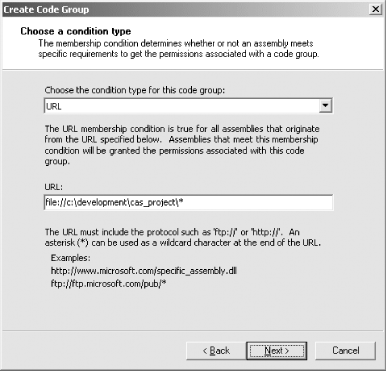 You can also choose to import a custom membership condition such as the AuthorMembershipCondition class that we developed in Chapter 8. Selecting (custom) from the list of membership condition types causes the dialog box to change its appearance to that shown in Figure 9-12. Pressing the Import button allows you to specify the file that contains an XML description of the custom membership condition. In Figure 9-12, we have imported the XML description of an AuthorMembershipCondition that matches any code with Author = Peter evidence. Figure 9-12. Importing a custom membership condition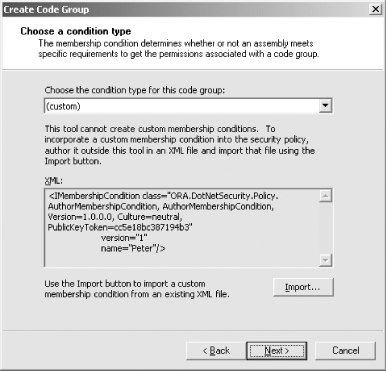
After configuring the code group's membership condition, press the Next button to display the dialog box shown in Figure 9-13, which allows you to select the permission set that the code group grants to its members. You can choose an existing named permission set from the current policy level, or you can choose to create a new code group. If you choose to create a new code group, you will begin the process we described earlier in Section 9.3.2.1. Figure 9-13. Selecting the code group's permission set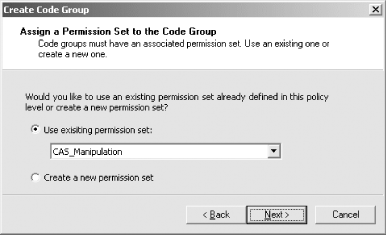 Selecting the named permission set for the code group and pressing the Next button completes the creation of the code group and returns you to the Mscorcfg.msc main window. 9.3.4 Other Security Policy Administration OptionsThe previous sections have shown you how to perform the security policy configuration tasks you will use most frequently during the development and testing process. Here we outline a number of other operations available through Mscorcfg.msc that you may find useful. By right-clicking the Runtime Security Policy node in the console tree, you will see the shortcut menu shown in Figure 9-14. Figure 9-14. The shortcut menu available through Mscorcfg.msc The commands available to you are:
|
| [ Team LiB ] |
|